Introduction
Few security controls have weathered the constant churn of technology better than the firewall. Created in the late-1980s to keep experimental malware out of small, research-grade networks, these policy-driven filters now sit in data-center racks, public-cloud regions, branch offices, and even the firmware of smart thermostats. Their job is deceptively straightforward: examine every packet that tries to cross a boundary and decide, in milliseconds, whether to let it through. When criminals can buy pre-packaged ransomware on Telegram and launch hundreds of attacks in a single afternoon, having that first gatekeeper in place is non-negotiable.
This guide demystifies how firewalls make allow/deny decisions, the different architectural flavors available, and best practices for keeping rulesets effective long after deployment day. By the end, you’ll know exactly which questions to ask before choosing hardware, virtual, or cloud-delivered models-and how to maintain them without drowning in false-positive alerts.
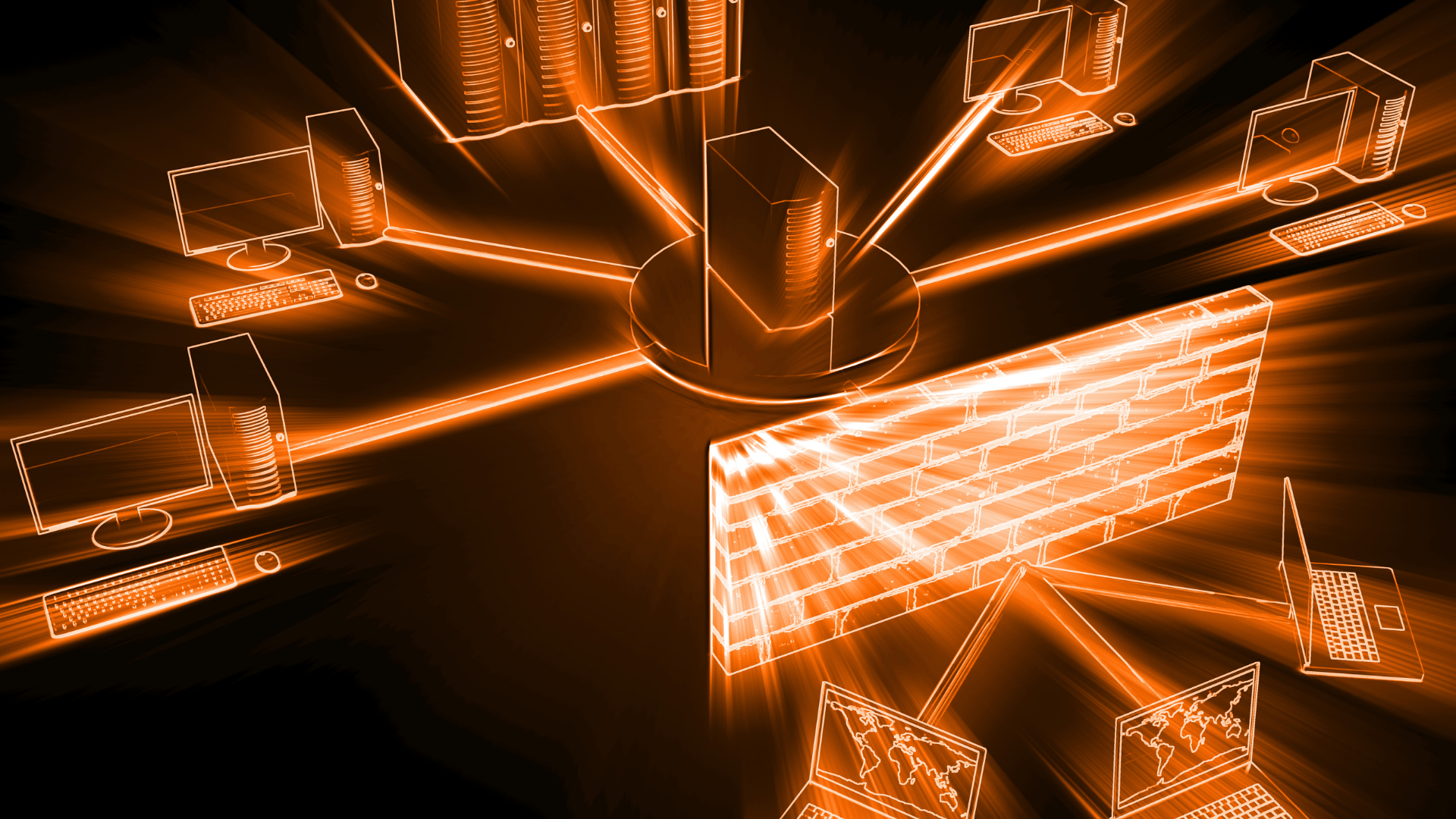
Firewall Fundamentals
A firewall is, at heart, a traffic cop that enforces an organization’s security policy. It compares each inbound or outbound packet against a list of rules called access-control lists (ACLs). If the packet’s metadata-source IP, destination IP, port, protocol, user identity, or any combination of those-matches a rule that says “allow,” it proceeds; if not, it is silently dropped or explicitly rejected. Because most networks use a default-deny stance, anything that is not expressly permitted is prohibited.
You’ll find firewalls deployed in three primary locations:
- Perimeter gateways that guard the edge between a private LAN and the public internet.
- Cloud ingress/egress points where SaaS traffic enters multi-tenant environments.
- Host-based agents baked into operating systems such as Windows Defender Firewall or iptables on Linux to protect individual endpoints.
A single enterprise may run all three, forming a layered defense that stops commodity threats at the edge while still monitoring internal “east-west” traffic for lateral movement.
Most conversations about firewalls focus on appliances, but cloud and software versions use the same logic. They all parse packet headers, consult policies, and then act. The difference lies mainly in throughput capacity and management convenience.
The broad relevance of firewalls is why leading analysts repeatedly emphasize the importance of firewall in security, a theme explored in depth in Fortinet’s glossary on firewall technology.
How Firewalls Work
To understand the mechanics, imagine a packet entering an NGFW (next-generation firewall). The device performs four sequential steps:
- Parse Headers. Source/destination IP, port numbers, protocol flags, and optional metadata such as VLAN tags are extracted.
- State Check (Stateful Designs). If the packet belongs to an existing session in the firewall’s state table, the verdict from the initial handshake is reused, accelerating throughput.
- Rule Evaluation. The remaining packets are compared to ACL entries from top to bottom. Rules can be as specific as “allow HTTPS from 10.1.1.0/24 to app-server-01” or as broad as “deny any traffic to port 23.”
- Deep Packet Inspection. Modern NGFWs open the payload (including decrypted TLS streams) to identify malware signatures, command-and-control callbacks, or sensitive data patterns (think credit-card numbers).
If any step fails to satisfy policy, the packet is blocked and, depending on configuration, the user receives a notification while administrators log the event for forensic review.
Key Features and Capabilities
- ACLs and Policy Management keep rules human-readable and auditable.
- DPI and Application Awareness recognize traffic as “Salesforce,” “Zoom,” or “Tor” regardless of port, enabling business-aligned decision making.
- Intrusion-Prevention Systems (IPS) block exploits by matching traffic against signature feeds from organizations like NIST’s National Vulnerability Database.
- VPN Support terminates IPsec site-to-site tunnels or SSL VPN sessions for remote staff.
- SSL/TLS Inspection decrypts and scans encrypted payloads-a necessity since 93% of malware now hides inside HTTPS, according to the Google Transparency Report.
- Logging and SIEM Integration stream events to analytics engines such as Splunk Enterprise Security for correlation and rapid response.
Why Firewalls Matter for Cybersecurity
- Malware Gatekeeping. Blocking ransomware droppers at the perimeter prevents endpoint compromise.
- Unauthorized Access Prevention. Geo-IP bans, brute-force thresholds, and adaptive authentication stop attackers from exploiting exposed services.
- Regulatory Compliance. Frameworks like PCI DSS require segmentation, which firewalls provide by isolating cardholder environments from general-purpose networks.
- Secure Remote Connectivity. Integrated VPN and zero-trust gateways give users access to internal apps without exposing the whole LAN.
Choosing the Right Firewall Solution
- Home Users may rely on software firewalls built into their OS and a small hardware router from their ISP.
- Small Businesses often deploy unified threat-management boxes that combine NGFW, IPS, and web filtering in one.
- Enterprises need high-throughput NGFW clusters or cloud NGFWs that enforce identical policies across multiple regions.
Key selection criteria include maximum throughput with DPI enabled, number of SSL decrypt sessions, redundancy options, licensing simplicity, and vendor reputation for timely patches.
Best Practices for Configuration and Maintenance
- Principle of Least Privilege. Start with a deny-all rule, then add granular permits.
- Firmware & Signature Hygiene. Schedule patches and IPS updates weekly or even daily.
- Continuous Monitoring. Stream logs to a SIEM, create alert thresholds, and investigate anomalies quickly.
- Rule-Base Cleanup. Audit quarterly to remove unused or expired rules; forgotten “any/any” statements are a leading cause of compromise.
Future Trends
- SASE Convergence. Firewalls will blend with secure web gateways and CASBs into single, cloud-native platforms.
- AI-Driven Detection. Machine-learning models will flag zero-day tactics by analyzing deviations from normal traffic.
- Zero-Trust Microsegmentation. NGFWs will enforce identity-based policies down to individual workloads.
- 5G & Edge Security. Lightweight containerized firewalls will protect ultra-low-latency applications at the network edge.
Conclusion
Firewalls remain the internet’s gatekeepers, screening every packet against business policies and threat intelligence. While architecture choices have diversified-from on-prem appliances to cloud-hosted services-the fundamental mission stays the same: stop malicious traffic, allow legitimate flows, and provide the visibility necessary to respond when something slips through. Auditing your current deployment, tightening permissive rules, and keeping firmware current are practical steps you can take today to ensure your firewall continues to deliver reliable, front-line protection tomorrow.
Frequently Asked Questions
1. Do I still need a firewall if all my workloads are in the cloud?
Yes. Cloud providers secure their infrastructure, but you are responsible for controlling inbound and outbound flows to your virtual networks. Cloud native firewalls or FWaaS offerings let you apply the same policies you would on-prem.
2. How often should firewall firmware be updated?
Apply critical security patches as soon as the vendor releases them. For routine updates, a monthly or quarterly schedule-paired with a staging environment for testing-is common practice.
3. Can an NGFW replace my standalone IPS?
Modern NGFWs embed high-confidence intrusion-prevention engines. For many organizations that integration provides sufficient protection while reducing complexity. However, very high-traffic environments might still require dedicated IPS appliances for extra throughput and rule granularity.

Founder Dinis Guarda
IntelligentHQ Your New Business Network.
IntelligentHQ is a Business network and an expert source for finance, capital markets and intelligence for thousands of global business professionals, startups, and companies.
We exist at the point of intersection between technology, social media, finance and innovation.
IntelligentHQ leverages innovation and scale of social digital technology, analytics, news, and distribution to create an unparalleled, full digital medium and social business networks spectrum.
IntelligentHQ is working hard, to become a trusted, and indispensable source of business news and analytics, within financial services and its associated supply chains and ecosystems